PicoCTF Disko-1 Writeup.....
❇️ Description
Can you find the flag in this disk image?
Author: Darkraicg492
🧩 Challenge Overview
In this challenge, we are given a raw disk image file:
disko-1.dd
Our task is to extract the flag hidden somewhere inside this image. Let's dive into a quick and effective way to solve it using the strings utility.
disko-1.dd
Our task is to extract the flag hidden somewhere inside this image. Let's dive into a quick and effective way to solve it using the strings utility.
🧰 Tools Used
strings – to extract readable ASCII/Unicode strings from binary files.
file – to identify file format.
🔍 Step 1: Identify the File
First, I use the 'file' command to understand what kind of image we’re dealing with.
output: 'disko-1.dd: DOS/MBR boot sector, code offset 0x58+2, OEM-ID "mkfs.fat", Media descriptor 0xf8, sectors/track 32, heads 8, sectors 10bit), sectors/FAT 788, serial number 0x241a4420, unlabeled'.
This output tells , that the image contains a FAT32 filesystem, often used on USB drives. It may not contain a full partition table — possibly a straight file system dump.
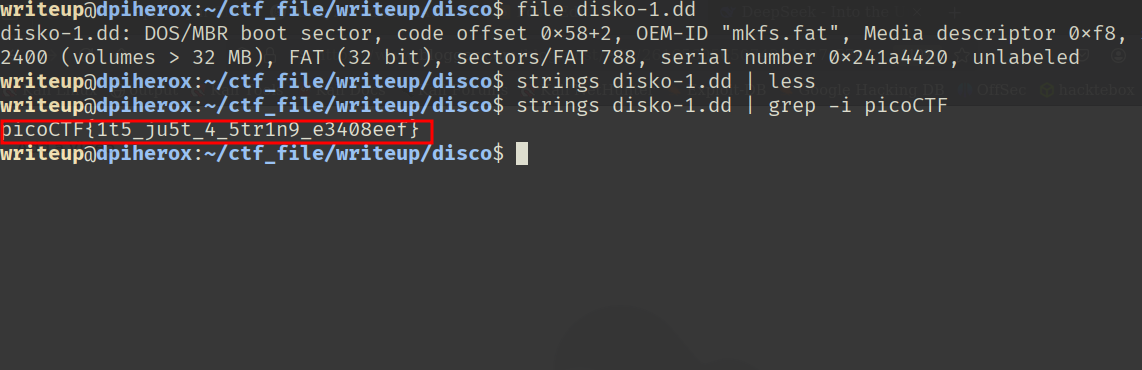
🔎 Step 2: Extract All Strings
Using this command to extract all strings:'strings disko-1.dd | less' and then, I used 'grep' to find the flag.
and I got the flag.





0 Comments