Tryhackme Corridor writeup step by step...
Description :-
You have found yourself in a strange corridor. Can you find your way back to where you came?
In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don't they?). This could help you uncover website locations you were not expected to access.
In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don't they?). This could help you uncover website locations you were not expected to access.
Problems :-
1.Can you find the flag?
Solutions :-
Step1 :-
Enumeration of the machine using 'nmap' shows the following scan results.
You can see that only port 80 is open, and it's running a website. Visit this website.
It's a simple website with just some images of doors. However, I noticed that each door has a number, and when clicked, the door redirects to 'http://ip/num_of_door', but the number is in MD5 format.
Inspecting the website, I collected all the MD5 hashes of the door numbers. I then cracked the MD5 hashes using CrackStation.
Cracking the MD5 hashes, they revealed a simple sequence of numbers from 1 to 13.
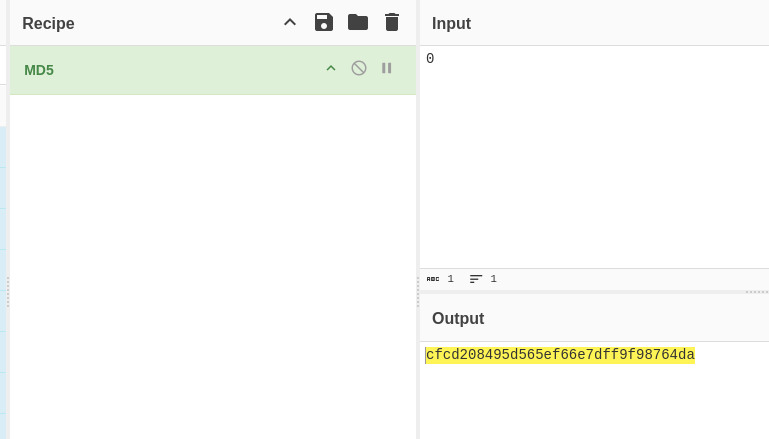
Thinking outside the box, I noticed the sequence shows numbers from 1 to 13, so I wondered why it didn’t start at 0. I tried using 0 to found the flag with the hash value for 0.
Then, copy the hash value, go to the website and paste it on url endpoint.
Game over , I found the flag.











0 Comments